CLI Upgrade VMware Servers to ESXi 6.7 U2
Scheduled non-working hours to upgrade and patch our VMware Servers for Intel CPU's vulnerabilities - Microarchitectural Data Sampling (MDS).
Sure. Veeam Backup to be 9.5 Update 4a also.
At the beginning, got this Dependency Error:
Identified that required ESXi-6.7.0-20190402001-standard
Updated the Firewall Policy for downloading the Requirement. Then, installed those together:
Checked ESXi Side-Channel-Aware Scheduler setting. SCAv1 decided. So, hyperthreadingMitigation & hyperthreadingMitigationIntraVM TRUE:
If not yet TRUE:
Reboot, then:
Last:
Appendix: Security & Performance
Performance of vSphere 6.7 Scheduling Options
https://www.vmware.com/techpapers/2018/scheduler-options-vsphere67u2-perf.html
Process security boundary
The process security boundary ensures that concurrent-context attacks using speculative side channels do not expose information across different processes or security contexts within the guest.
References
VMware ESXi 6.7 Update 2 Release Notes
Sure. Veeam Backup to be 9.5 Update 4a also.
At the beginning, got this Dependency Error:
# esxcli software vib update --depot=/vmfs/volumes/datastore1/Patches/update-from-esxi6.7-6.7_update02.zip
[DependencyError]
VIB VMware_bootbank_esx-base_6.7.0-2.48.13006603 requires esx-update << 6.7.0-2.49, but the requirement cannot be satisfied within the ImageProfile.
VIB VMware_bootbank_esx-base_6.7.0-2.48.13006603 requires esx-update >= 6.7.0-2.48, but the requirement cannot be satisfied within the ImageProfile.
Please refer to the log file for more details.
[DependencyError]
VIB VMware_bootbank_esx-base_6.7.0-2.48.13006603 requires esx-update << 6.7.0-2.49, but the requirement cannot be satisfied within the ImageProfile.
VIB VMware_bootbank_esx-base_6.7.0-2.48.13006603 requires esx-update >= 6.7.0-2.48, but the requirement cannot be satisfied within the ImageProfile.
Please refer to the log file for more details.
Identified that required ESXi-6.7.0-20190402001-standard
# esxcli software sources profile list --depot=/vmfs/volumes/datastore1/Patches/update-from-esxi6.7-6.7_update02.zip
Name Vendor Acceptance Level Creation Time Modification Time
-------------------------------- ------------ ---------------- ------------------- -------------------
ESXi-6.7.0-20190402001-standard VMware, Inc. PartnerSupported 2019-03-27T04:46:55 2019-03-27T04:46:55
ESXi-6.7.0-20190401001s-standard VMware, Inc. PartnerSupported 2019-03-27T04:46:55 2019-03-27T04:46:55
ESXi-6.7.0-20190401001s-no-tools VMware, Inc. PartnerSupported 2019-03-27T04:46:55 2019-03-27T04:46:55
ESXi-6.7.0-20190402001-no-tools VMware, Inc. PartnerSupported 2019-03-27T04:46:55 2019-03-27T04:46:55
Name Vendor Acceptance Level Creation Time Modification Time
-------------------------------- ------------ ---------------- ------------------- -------------------
ESXi-6.7.0-20190402001-standard VMware, Inc. PartnerSupported 2019-03-27T04:46:55 2019-03-27T04:46:55
ESXi-6.7.0-20190401001s-standard VMware, Inc. PartnerSupported 2019-03-27T04:46:55 2019-03-27T04:46:55
ESXi-6.7.0-20190401001s-no-tools VMware, Inc. PartnerSupported 2019-03-27T04:46:55 2019-03-27T04:46:55
ESXi-6.7.0-20190402001-no-tools VMware, Inc. PartnerSupported 2019-03-27T04:46:55 2019-03-27T04:46:55
Updated the Firewall Policy for downloading the Requirement. Then, installed those together:
# esxcli network firewall ruleset set -e true -r httpClient
# esxcli software profile update -p ESXi-6.7.0-20190402001-standard --depot=/vmfs/volumes/datastore1/Patches/update-from-esxi6.7-6.7_update02.zip
Update Result
Message: The update completed successfully, but the system needs to be rebooted for the changes to be effective.
Reboot Required: true
VIBs Installed: VMW_bootbank_bnxtnet_20.6.101.7-21vmw.670.2.48.13006603, VMW_bootbank_bnxtroce_20.6.101.0-20vmw.670.1.28.10302608, VMW_bootbank_brcmfcoe_11.4.1078.19-12vmw.670.2.48.13006603, [...]
# esxcli network firewall ruleset set -e false -r httpClient
# esxcli software profile update -p ESXi-6.7.0-20190402001-standard --depot=/vmfs/volumes/datastore1/Patches/update-from-esxi6.7-6.7_update02.zip
Update Result
Message: The update completed successfully, but the system needs to be rebooted for the changes to be effective.
Reboot Required: true
VIBs Installed: VMW_bootbank_bnxtnet_20.6.101.7-21vmw.670.2.48.13006603, VMW_bootbank_bnxtroce_20.6.101.0-20vmw.670.1.28.10302608, VMW_bootbank_brcmfcoe_11.4.1078.19-12vmw.670.2.48.13006603, [...]
# esxcli network firewall ruleset set -e false -r httpClient
Checked ESXi Side-Channel-Aware Scheduler setting. SCAv1 decided. So, hyperthreadingMitigation & hyperthreadingMitigationIntraVM TRUE:
# esxcli system settings kernel list -o hyperthreadingMitigation
Name Type Configured Runtime Default Description
------------------------ ---- ---------- ------- ------- --------------------
hyperthreadingMitigation Bool TRUE TRUE FALSE Restrict the
simultaneous use of
logical processors
from the same
hyperthreaded core
as necessary to
mitigate a security
vulnerability.
Name Type Configured Runtime Default Description
------------------------ ---- ---------- ------- ------- --------------------
hyperthreadingMitigation Bool TRUE TRUE FALSE Restrict the
simultaneous use of
logical processors
from the same
hyperthreaded core
as necessary to
mitigate a security
vulnerability.
# esxcli system settings kernel list -o hyperthreadingMitigationIntraVM
Name Type Configured Runtime Default Description
------------------------------- ---- ---------- ------- ------- ------------------------------------------------------------------------------------------------------------------------------------------------------
hyperthreadingMitigationIntraVM Bool TRUE TRUE TRUE Restrict the simultaneous use of logical
processors from the same hyperthreaded
core as necessary to mitigate a security
vulnerability within a single VM.
Name Type Configured Runtime Default Description
------------------------------- ---- ---------- ------- ------- ------------------------------------------------------------------------------------------------------------------------------------------------------
hyperthreadingMitigationIntraVM Bool TRUE TRUE TRUE Restrict the simultaneous use of logical
processors from the same hyperthreaded
core as necessary to mitigate a security
vulnerability within a single VM.
If not yet TRUE:
# esxcli system settings kernel set -s hyperthreadingMitigation -v TRUE
# esxcli system settings kernel set -s hyperthreadingMitigationIntraVM -v TRUE
Reboot, then:
# esxcli system maintenanceMode set --enable true
# esxcli system shutdown reboot --reason "Patch update-from-esxi6.7-6.7_update02.zip"
# esxcli system shutdown reboot --reason "Patch update-from-esxi6.7-6.7_update02.zip"
Last:
# esxcli software vib update --depot=/vmfs/volumes/{UUID}/Patches/ESXi670-201905001.zip
# esxcli system maintenanceMode set --enable true
# esxcli system shutdown reboot --reason "Patch ESXi670-201905001.zip"
# esxcli system maintenanceMode set --enable true
# esxcli system shutdown reboot --reason "Patch ESXi670-201905001.zip"
Appendix: Security & Performance
Performance of vSphere 6.7 Scheduling Options
https://www.vmware.com/techpapers/2018/scheduler-options-vsphere67u2-perf.html
Host security boundary
Relying on the host security boundary is not recommended. Using L1TF concurrent-context attack vector, a VM on the host can observe any information on that host.
Relying on the host security boundary is not recommended. Using L1TF concurrent-context attack vector, a VM on the host can observe any information on that host.
VM security boundary
The VM security boundary prevents information leaking between two different VMs on a host or between a VM and the hypervisor. Concurrent-context speculative side-channel attacks can be used to reveal information across different security domains of a single ESXi VM.
This option provides a balance of performance and security for environments where the VM is considered the information security boundary.
The VM security boundary prevents information leaking between two different VMs on a host or between a VM and the hypervisor. Concurrent-context speculative side-channel attacks can be used to reveal information across different security domains of a single ESXi VM.
This option provides a balance of performance and security for environments where the VM is considered the information security boundary.
Process security boundary
The process security boundary ensures that concurrent-context attacks using speculative side channels do not expose information across different processes or security contexts within the guest.
Default – Unmitigated and most performance – Not concerned about L1TF security vulnerability.
* HyperthreadingMitigation = FALSE
* HyperthreadingMitigationIntraVM = N/A
* HyperthreadingMitigation = FALSE
* HyperthreadingMitigationIntraVM = N/A
SCAv1 - Auto Hyperthreading off – What was made available at L1TF announcement in August 2018.
* HyperthreadingMitigation = TRUE
* HyperthreadingMitigationIntraVM = TRUE
* HyperthreadingMitigation = TRUE
* HyperthreadingMitigationIntraVM = TRUE
SCAv2 - New policy in vSphere 6.7 U2
* HyperthreadingMitigation = TRUE
* HyperthreadingMitigationIntraVM = FALSE
* HyperthreadingMitigation = TRUE
* HyperthreadingMitigationIntraVM = FALSE
References
VMware ESXi 6.7 Update 2 Release Notes
https://docs.vmware.com/en/VMware-vSphere/6.7/rn/vsphere-esxi-67u2-release-notes.html
VMSA-2019-0008
Release Notes for Veeam Backup Replication 9.5 Update 4a
https://www.veeam.com/kb2926
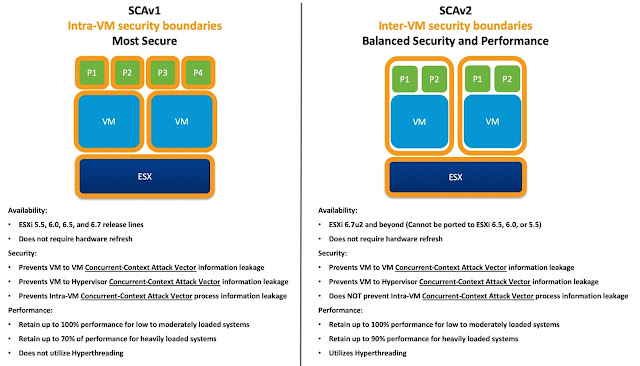
SCAv1 vs SCAv2
(source: vmware)
Update
VMSA-2019-0008
- CVE-2018-12126 - Microarchitectural Store Buffer Data Sampling (MSBDS) - CVSSv3 = 6.5
- CVE-2018-12130 - Microarchitectural Fill Buffer Data Sampling (MFBDS) - CVSSv3 = 6.5
- CVE-2018-12127 - Microarchitectural Load Port Data Sampling (MLPDS) - CVSSv3 = 6.5
- CVE-2019-11091 - Microarchitectural Data Sampling Uncacheable Memory (MDSUM) - CVSSv3 = 3.8
Release Notes for Veeam Backup Replication 9.5 Update 4a
https://www.veeam.com/kb2926
SCAv1 vs SCAv2
Update